
Colonial pipeline ransomware overview
Every day it becomes more apparent that nobody is immune to ransomware From mom and pop shops to the largest US refined products pipeline system, that supplies gas to most ...
Notices Alias todayMay 17, 2021 372 2 1

Due to the cybersecurity issue at Colonial Pipeline, the Colonial Hack, most of the fuel supply to the east coast has been disrupted for more than a week.
It has been reported that the company paid five million dollars in ransom and received decryption keys. Darkside, the hacking group attributed for perpetrating this attack, claims that they were only in it for the money. That they never intended to cause large-scale problems, nor do they want to be politically involved.
Many analysts are suggesting that the pipeline was simply low-hanging fruit.
The attackers found an easy way in and the results just happened to be something critical. The attackers weren’t even specifically targeting industrial systems.
All of this should make you ask, how significant would the damage be if the attacker was specifically targeting organizations that rely on industrial systems or operational technology?
First, here is some additional background on Information Technology (IT) and Operational Technology (OT).
IT is traditionally the computers and systems running business functions like accounting, email, sales, marketing, and probably what comes to mind first for most people.
OT is the hardware and software used to control and monitor physical devices, events, and processes.
The technology is mainly used in industrial settings. OT primarily runs on SCADA (Supervisory Control and Data Acquisition). This includes water systems, wastewater controls, electric generation, nuclear power plants, transmission, distribution systems, oil and gas systems, manufacturing plant systems, food production systems, mass transit, and many more. These may not be what people think of first, but we all depend on this technology every day.
Most OT devices rely on a PLC (programmable logic controller). PLCs are essentially digital computers that communicate with input devices or sensors to carry out specific tasks or output information. This could be anything from pressing a button that initiates a process to move a lever or changing the temperature on a boiler to a complex sequence of movements for a robotic arm.
PLCs operate in four basic steps.
Input devices could include switches and pushbuttons, limit switches, photoelectric sensors, proximity sensors, pressure switches, level switches, temperature switches, float switches, etc.
Outputs would be things like temperature or volume readings, valves, motor operations, solenoids, actuators, alarms, lights, pumps, fans, etc.
This can obviously be some very important stuff that runs our modern world. These are the types of systems and devices that don’t change and sometimes are not updated, as long as their purpose is served. The devices are very specialized and generally even require custom software to function.
Most SCADA systems use a very simple protocol called MODBUS. This is based on serial networks that originally were isolated and usually do not have native support for authentication, integrity validation, or confidentiality protection. Devices were developed to accept commands via MODBUS without these controls.
In other words, if an attacker or corrupt packet is sent to a device, it could cause a denial of service or issue an invalid command. Basically, MODBUS has a simple structure with almost no validation:
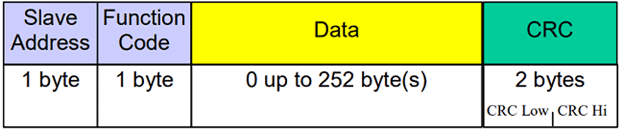
Then as the world became connected, MODBUS was updated to utilize standard TCP/IP networks as a transport with the same basic command structure:
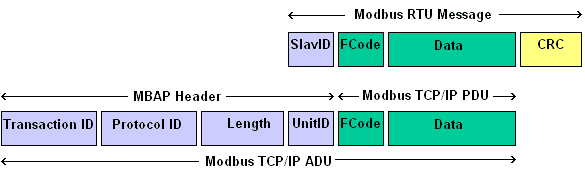
As OT becomes connected, it carries these dated concepts and lacks some of the controls built into IT systems. There are lots of ways to protect OT and IT, but mistakes happen, and with connectivity, they become more exposed.
Take as an example:
Peter opens a malicious email that drops code onto the network.
The network has been linked to an OT network without added controls.
The malicious code provides an attacker the ability to remote access or control devices.
Because OT does not natively have the same level of protection and is connected, the attacker can send commands to devices such as a boiler. By disrupting the system, it could be possible for the boiler to overheat and explode.
Instead of a boiler, maybe the system was a pipeline controlling your fuel, a nuclear plant, or the energy grid, or the company’s control systems where you just invested your life savings.
Again, we depend on OT, and you depend on organizations keeping them secure.
Organizations that run OT must add controls to segment these systems physically or logically. The operation of OT systems has to incorporate security, and similar to IT systems, this security should be tested often to ensure controls take into account new attack methods.
Given the physical, economic, and safety risks associated with OT, these systems need to be monitored and protected with advanced technologies.
Our security engineers perform security assessments on IT and OT networks. Alias has great partners such as Fortinet and Nozomi that offer advanced protection. Watch the video linked here to learn how we work with Fortinet to secure OT.
The Colonial Hack demonstrated that attackers do not care if they disrupt IT or OT, but Alias can help you secure both!
Written by: Alias

Notices Alias
Every day it becomes more apparent that nobody is immune to ransomware From mom and pop shops to the largest US refined products pipeline system, that supplies gas to most ...


Copyright 2019 Cyber Security Design Concept by <a href="http://qantumthemes.com?rel=demo" target="_blank">QantumThemes</a>.